True story: Ransomware almost destroyed their tourism company
Imagine if all of your company cloud apps, financial data and security video footage – representing 10 years work – was instantly inaccessible to every single computer user in your business. It’s the stuff of nightmares, but it was all too real for a successful Australian tourism company last month.
On New Year’s Day, while most of the Western world was relaxing and celebrating, the Emsisoft team was busy fighting a very big fire – our chief technology officer (CTO) Fabian Wosar had dissected Ransom32, the first JavaScript ransomware to be unleashed on the world, and quickly reverse engineered the software to create a decrypter – free of charge as usual.
As we mentioned in our earlier blog post “Ransomware for Hire: 3 Steps to Keeping Your Data Safe“, companies risk having to reinvent man-years worth of intellectual property should their data be lost – and for thousands of companies this nightmare becomes reality every day.

Only a few weeks after we had published this blog, the IT & Compliance Manager at an Australian tourism company contacted us with a story that made our hair curl.
The malicious ransomware software hijacked the company’s cloud solutions (Dropbox and One Drive accounts), all of their financial records and security footage amongst other things – all up a total of almost 20 TB of data and 10 years’ work, which was instantly inaccessible to the company’s 500 users.
As the manager writes below, it was a ‘TRUE DISASTER, one for which we were ill-prepared…’
Read on to learn how the company responded.
Hi Fabian,
I wish to thank you for your help and support during the past week when we were hit with a RANSOMWARE virus. Your promptness in responding to our dilemma has literally saved our business!
It took us a week to find THE EXPERT and identify the virus / solution, and a further week for me to go around to every computer and reverse the damage.
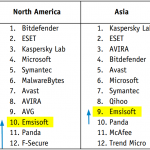
I have since purchased 10 licenses of EMSISOFT due to its behaviour analysis which could have saved us from all the drama.
As you are aware this specific MALWARE scans all drives (including mapped) and in our case, a peer Windows 10 network, with all the machines storing personal files locally and group files on the server.
Our downfall was that all the PCs have shares to other data areas on other drives. ONE user clicking the Zip/EXE, therefore changed the DATA on 8 machines plus the server (via Shares). Local PCs are NOT backed up (not many do) with the server holding critical historical data.
Examples of data unusable were:
All ONLINE data shared via DROPBOX and 365 OneDrive Business for all our external agents – Currently 500 users – 2 x 1TB accounts
MYOB Account backup Zip file from last year and beyond
Legal & insurance records
Banking and other XLS files
Client marketing (PDF)
VOIP recording data
Video security footages
Website development (images)
Audit data
Tender documents / presentations (DOC, PPT)
etc., etc., etc.

Even backup data was affected
You may ask why no backup? There is, but again, it is file based / user (NAS)…e.g. \\SERVER\(N:)\User
All the client backups are “mapped” – therefore ALL copies of the files were also affected including all users’ PC File Histories saved from their respective PCs.
The server is backed up on a 3 drive rotation so by the time we found the issue they had also been copied over.A file is either on a Client PC, the NAS, PC file History, the Server or Online…..However in OUR case- ALL NO GOOD.
An archive is taken every month, so we could have gone back 6 weeks for the server data but not the live NAS backups or the 8PC current data
To retrieve all the online storage again would have taken a considerable time.OBVIOUSLY TAKING COPIES OF DATA IS NO LONGER AN OPTION…
We are currently searching for image based systems that can be both Archival and Incremental, while being able to restore to a point in time, rather than just changes in files – since the virus did change them, they were subsequently added into the backup.In ALL, 1 Server (2TB), 8 PC (100GB each), various ONLINE storage (Business -2TB and Personal – 4TB), Client NAS Storage (4TB) and 6TB of Server Backup
Totalling almost 20 TB of data, and 10 years of work – inaccessible and users unable to function … a TRUE DISASTER, one for which we were ill-prepared…
Literally, a fire would have done less damage…this is a wake-up call and one which other companies should be made aware…
Again FABIAN, we cannot thank you enough for your tireless work in combatting the data threats in which we currently live, please accept our gratitude….
ALL DATA RECOVERED – NOT A Single file missing…
Regards
[Name withheld] IT & Compliance Manager
What you can do to prevent nightmares like that:
1. Don’t store backups on local hard drives or mapped network shares, as they can be reached by malware too.
This case study validates our observation that security is only as good as the weakest link. To reduce the impact of a (hopefully never to strike) malware attack, make sure you don’t store backups on any drives that can be reached by your local user accounts without manually entering a password.
2. Close the entry gates: Keep your systems and your programs up to date and use a good real-time protection.
Often, the weakest links are well-intentioned employees who are focused on doing a good job, but don’t realize the security risks inherent in today’s online world. To close the entry gates, top priority is keeping your operating system and all your programs always up to date (not just once in a while – always, as in ‘every day’). Also make sure you’re running a trustworthy real-time protection that catches all malicious files as they try to enter your computers. Because you know what they say: An ounce of prevention is always worth a pound of cure.
Related Posts:
- Ransomware for Hire: 3 Steps to Keeping Your Data Safe
- Warning: Dropbox and Box File Sharing Security Bug
- Special: backup software for free with your order at…
- How it’s done right: Emsisoft’s Behavior Blocker
- Protect your laptop data from theft – Here’s how