When it comes to defending against phishing attacks, your employees are one of the best lines of defense. Phishing targets users directly and has been so effective because it’s easier to trick a user than to conduct a brute force attack to do things like obtaining user login credentials or planting malware in a system.
Phishing continues to be a major threat to company network security for many Columbus area businesses. Phishing attacks increased over 280% in both May and June of 2021.
While you may train your employees on how to detect phishing once or twice a year, once that training is over, people don’t always retain all the information.
One way to improve phishing detection skills and help employees remember what they need to check to uncover a scam email is to use the SLAM method.
SLAM is an acronym that helps remind users of the key areas of an email to review to identify phishing. These are:
- Sender
- Links
- Attachments
- Message
Promoting SLAM in your employee security awareness training and reminders (posters, newsletter, other messaging) can reduce the chances of your company falling victim to a cyberattack.
One other way that SLAM helps, is that it gives employees “permission” to not take immediate action on a suspicious email that might be enticing them to click a link to fix some sort of fake problem. If they’re encouraged to use SLAM, then it requires them to take a step back and really review a message before being enticed into any action.
Companies that have well-trained employees in cybersecurity can reduce their risk of being impacted by an attack by up to 70%.
Training Employees on SLAM for Phishing Identification
Sender
It’s important to thoroughly review the sender of an email to ensure the name you see is legitimate. The first step is to see whether or not you recognize the email address (don’t just go by the display name) that the message came from.
If you don’t recognize it, then a message should be considered high risk for phishing, until you’ve identified through other means that it’s legitimate.
It’s important to note that there are ways that phishing attackers try to get users to trust a message. They’ll either spoof a vendor’s email closely or take over an account (known as business email compromise).
For example, in this email below, the sender’s address looks like it almost might be legitimate, since “bankofamerica” is used in the address.
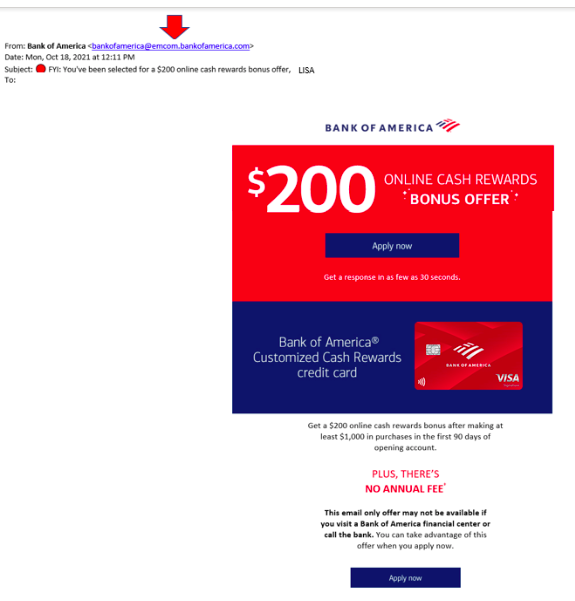
However, a quick Google search of that name quickly reveals it to be a phishing scam that is used both via email and SMS.
Links
Hyperlinks are now being used widely in phishing emails more often than file attachments. One reason is that links can often get by malware filters because they’re not technically malware, they’re just links to a malicious phishing site.
Users should always hover over links first to see where they are really going. Phishing emails will often hide scam links behind text that looks like a legitimate link or behind an image like a button.
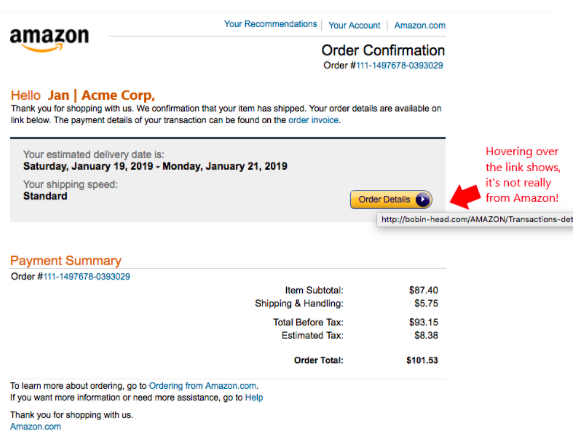
When possible, always go to a website directly rather than going through an email link to be safe. For example, if you receive a tracking notification via email, go to the shipper’s site directly and type in the tracking number to review status, rather than using the link in the email.
Attachments
Companies have long warned employees about the dangers of opening unknown file attachments in email messages, as these can often contain malware.
When reviewing attachments, it’s important to note that even seemingly innocent file types, such as Word or PDF, can also be weaponized with malware. It’s important to never open any file attachment without it being scanned by a reliable anti-malware filter first.
Message
Phishing emails have become more sophisticated over the years and it’s harder to catch things like spelling or grammatical errors. However, these things do still exist, you just may have to look a little harder for them.
Read the body of the email message thoroughly, don’t just skim through. This can help you catch anything that sounds a little “off” or that uses a word that doesn’t make sense. This is often a sign of a phishing email.
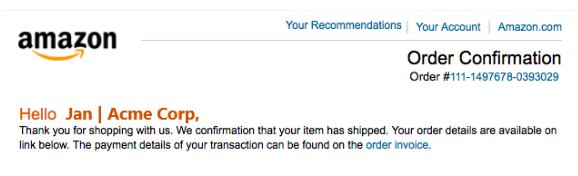
For example, let’s look a little closer at the fake Amazon email example posted above. Did you notice that in the first sentence there is a grammatical error giving the message away to be a scam?
It says, “We confirmation that your item has shipped” instead of “We confirm that your item has shipped.”
If you don’t look carefully, you can easily miss a phishing sign like this.
How Strong Are Your Email Phishing Protections?
Reducing the number of scam emails that make it into user inboxes reduces the burden on your employees. AhelioTech can help your Columbus area business put strong phishing filtering in place to improve overall email security.
Contact us today for a free quote. Call 614-333-0000 or reach out online.





