Phishing attacks continue to be a major driver of data breaches, ransomware, spyware, credential theft, and other types of online attacks. No matter how big or small your company is, it’s not immune to receiving phishing emails or having an employee accidentally click on one.
In 2020, 96% of cyberattacks globally originated with a phishing email, and 75% of companies experienced phishing attacks.
Why has phishing remained such a threat to data and network security? It’s because it exploits human error very effectively. Phishing emails also continue to evolve as safeguards to stop attacks evolve.
For example, most phishing used to contain malicious file attachments that released a virus or other malware if opened. But as antivirus and anti-malware software got stronger, these types of attacks became less effective. So, phishing scammers switched tactics and now largely use hyperlinks to malicious sites or files. A hyperlink can more easily get past filters that are looking for dangerous attachments.
Educating your team on the best ways to avoid a phishing attack can significantly decrease your company’s risk of having a major security incident. Part of that training needs to include details on what types of emails to watch out for.
By knowing some of the most dangerous and commonly used phishing emails, users can better identify them when one is sitting in their inbox enticing the user to click.
Shipment Needs Your Attention
Seeing shipment notices in our email inboxes isn’t out of the ordinary. We get them for things like delivery notifications and delivery delays. Scammers take advantage of the commonality of shipment notices and use them as a cover for a popular phishing campaign.
The user receives an email that looks like it’s from USPS. Everyone receives mail from the post office, so they don’t immediately suspect it. Phishing emails will also use logos and signatures of the organizations they’re spoofing.
The email warns that there is some type of shipment issue that “needs your attention” otherwise the shipment won’t be delivered. The link is of course a fake that goes to a phishing website.
Update Your Payment Settings
Another scam that uses a fake login form and is designed to steal your personal information, including credit card number, is the fake “update your payment settings” email.
This can be spoofed to look like it comes from any type of vendor, including Netflix or Amazon.
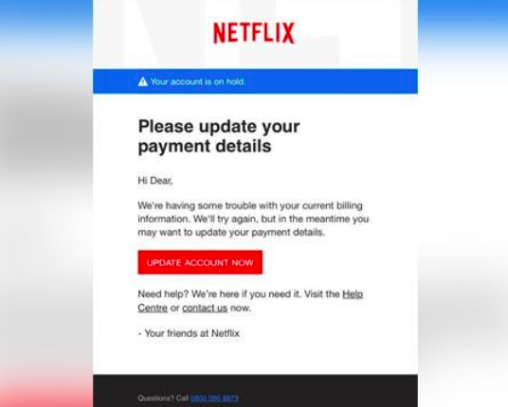
Image courtesy of the FTC
It uses the tactic of urgency to get the user to react without thinking by noting that the account is on hold.
As with any unexpected messages with links you receive via email, you should never click the link. Instead, visit the company’s website from its web address, and log in to check your account that way. Or go “old school” and call them to ask if your account is really on hold or not.
Someone Just Used Your (Apple, Microsoft, etc.) ID
This phishing email scam is designed to steal someone’s login credentials to a popular site like iTunes or Microsoft. It masquerades as a helpful security warning that someone has just used your ID.
When the person clicks the link, they’re taken to a fake login form where the scammer can steal their ID for real.
Fake Purchase Order
Many companies have fallen victim to the fake purchase order scam. Who doesn’t want what looks to be a “large order” from a new customer? The email will claim that a large and urgent PO is attached, and it might even include the name of one or more of the company’s products in the body of the email to lend legitimacy.
Unfortunately, some employees might mistakenly think that if it’s that detailed to include the product name, then it couldn’t be a scam since they wouldn’t go to that trouble. But, in fact, they do. Scammers know that the more personalized a message is, the better chance it has of fooling the recipient.
The fake PO is usually a malicious file attachment that infects the user’s system with malware.
Holiday Schedule Link or Attachment
With the holidays right around the corner, one popular scam will be increasing in volume in the coming weeks. This is one where the scammer will spoof the email address of the company, so the recipients think the email is from a work colleague or a department in their organization.
The email will include a link or attachment of a “holiday schedule,” which is a seemingly innocent document, but one that anyone would open to read so they see what extra time they may get off during the holidays.
In this case, “ask before you click” is the best method. Ask your supervisor or someone in HR if there was actually a holiday schedule sent around before you attempt to open it.
Put Automated Protections in Place to Combat Phishing
AhelioTech can help your Columbus area business with safeguards like email filtering, DNS filters, and more to reduce your risk of a phishing-related attack.
Contact us today for a free quote. Call 614-333-0000 or reach out online.





